Types of Firewall

Also known as application proxy or application-level proxy, an application gateway is an application program that runs on a firewall system between two networks.

But circuit-level firewalls do not clean entity packets. This is useful for hiding information about protected networks. Circuit-level gateways are relatively inexpensive and have the advantage of hiding information about the private network they protect. On the other hand, they do not filter individual packets.

A next-generation firewall (NGFW) is a hardware- or software-based network security system that is able to detect and block sophisticated attacks by enforcing security policies at the application level, as well as at the port and protocol level.
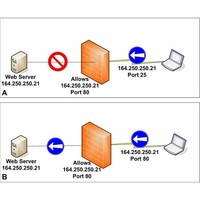
Packet filtering is a firewall technique used to control network access by monitoring outgoing and incoming packets and allowing them to pass or halt based on the source and destination Internet Protocol (IP) addresses, protocols and ports.

Packet filtering is the process of passing or blocking packets at a network interface based on source and destination addresses, ports, or protocols. Packet filtering is the process of passing or blocking packets at a network interface based on source and destination addresses, ports, or protocols.

A proxy firewall is a network security system that protects network resources by filtering messages at the application layer. A proxy firewall may also be called an application firewall or gateway firewall.

Stateful firewall. In computing, a stateful firewall is a network firewall that tracks the operating state and characteristics of network connections traversing it. The firewall is configured to distinguish legitimate packets for different types of connections.