Types of Kali
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack.

Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.

8 Most Popular and Best Hacking Tools. ... Kali Linux. Kali Linux was ... Cain & Abel. Cain & Abel is a password recovery and hacking tool, ...

Hi The Hack Today, Today we are going to Setup Ettercap on Kali Linux, If you didn't know about Ettercap you should google around about that and read documentation on...
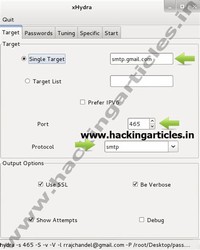
THC Hydra (we’ve abbreviated to simply ‘Hydra’ throughout our site) is a hugely popular password cracker and has a very active and experienced development team. Essentially THC Hydra is a fast and stable Network Login Hacking Tool that will use dictionary or brute-force attacks to try various password and login combinations against an log in page.

John the Ripper is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs (you can even define a custom cracking mode using the built-in compiler supporting a subset of C).

A listing of the Penetration Testing Tools available in Kali Linux

Kismet is an 802.11 layer-2 wireless network detector, sniffer, and intrusion detection system. It will work with any wireless card that supports raw monitoring (rfmon) mode, and can sniff 802.11a/b/g/n traffic.

Maltego Teeth Package Description Maltego is a unique platform developed to deliver a clear threat picture to the environment that an organization owns and operates. Maltego’s unique advantage is to demonstrate the complexity and severity of single points of failure as well as trust relationships that exist currently within the scope of your infrastructure.

Kali Linux is a security auditing toolkit, known to penetration testers as one of the most comprehensive open source pen testing tools, which allows you to test your network defenses. Metasploit has been re-engineered to fully integrate with Kali Linux to provide a better user experience. Check out one of the most popular pen testing tools out ...

In keeping with the Kali Linux Network Services Policy, no network services, including database services, run on boot as a default, so there are a couple of steps that need to be taken in order to get Metasploit up and running with database support.

I f you are using Nessus for vulnerability scanning activities, consider installing Nessus on Kali Linux. Kali Linux is a fantastic distribution specifically designed for penetration testing. Nessus, Kali, and Penetration Testing. Tenable provides Nessus on a wide variety of platforms to choose from.