Types of Threats
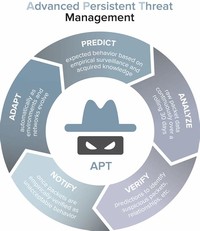
An advanced persistent threat (APT) is a network attack in which an unauthorized person gains access to a network and stays there undetected for a long period of time. The intention of an APT attack is to steal data rather than to cause damage to the network or organization.

Many of these threats are just productive, positive technologies turned to evil use. The botnet is an example of using good technologies for bad intentions. The botnet is an example of using good technologies for bad intentions.

What is a cyber attack? Simply put, a cyber attack is an attack launched from one computer or more computers against another computer, multiple computers or networks.

In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet.

"If the attackers start to increase the [malvertising] attacks ... it can go out of hand very quickly." What is malvertising? Usually, you only need to worry about malware from disreputable websites, or from websites that have had page code altered by hackers. But malvertising doesn't require complicit administrators or breaking into servers. Rather, it exploits the chaotic nature of the online advertising industry to place malicious ads on any website — even the most trustworthy ones.

Understanding the major types of malware can help you make informed decisions about acquiring tools to protect your computer. To prevent infection from any of these threats, be sure to use up-to-date antivirus software and ensure your firewall is enabled on your computer.

Phishing is a type of Internet fraud that seeks to acquire a user’s credentials by deception. It includes theft of passwords, credit card numbers, bank account details and other confidential information. Phishing messages usually take the form of fake notifications from banks, providers, e-pay systems and other organizations.

Monthly ransomware and ransomware downloader encounters, July 2016 to June 2017 Ransomware is a global problem. The US, China, Russia, Republic of Korea, and Italy saw the most ransomware encounters in the first six months of 2017.

A Trojan horse or Trojan is a type of malware that is often disguised as legitimate software. Trojans can be employed by cyber-thieves and hackers trying to gain access to users' systems. Users are typically tricked by some form of social engineering into loading and executing Trojans on their systems.